
Establish your digital perimeter
CyberArk prioritises security for your highest-value assets and your most important intellectual property, key initiatives, and other data that, if leaked, would do the greatest reputational and financial damage.
By evolving your PAM program to master risk, you can increase efficiency, cut costs, and create a source of competitive advantage.


PwC is proud to be recognised as the 2022 CyberArk Global System Integrator Partner of the Year, an honor that PwC has received for the eighth time. This award reflects PwC’s commitment to solving identity security and privileged access challenges for our clients.
Hardened Privileged Access Management (PAM)
- Create a secure repository to control, manage and monitor privileged access to your most critical assets
- Centralise privileged credentials in one place, control who and what is accessing them, log all accesses, monitor and alert for any suspicious activity
- Move away from routine passwords, as well as the substantial enterprise cost associated with passwords such as help desk calls
- Track and record activity that touches your privileged credentials (admin passwords, keys, secrets, etc.), which are often shared
Assuring confidence in data, systems, and processes drives business forward.

Establish your digital perimeter
CyberArk prioritises security for your highest-value assets and your most important intellectual property, key initiatives, and other data that, if leaked, would do the greatest reputational and financial damage.
By evolving your PAM program to master risk, you can increase efficiency, cut costs, and create a source of competitive advantage.
Implementing an Identity and governance platform is a foundational security capability for securing digital identities in the modern hybrid environment. Provisioning and maintaining the right access at the right time for both human and machine identities across cloud and on premise legacy environments is the challenge. At PwC we understand the challenge and work with our clients to implement a platform to manage the life cycle of identities with confidence.
Securing cloud-native apps and CI/CD pipelines at scale
As enterprises adopt DevOps practices and leverage CI/CD pipelines to increase their pace of innovation and accelerate their digital transformation, security becomes increasingly essential. Security teams work to avoid disjointed security systems and practices which can delay putting applications into production, and today, forward-looking security teams are shifting left in the software development lifecycle to engage earlier with development teams and improve collaboration.
PwC applies its strong capabilities in working with clients to help identify, design and deploy improved processes and technical solutions for DevOps environments. PwC’s experience working with CyberArk enables organisations to efficiently manage secrets and authorisation privileges across DevOps pipelines, helping security teams mitigate risks and helping improve compliance while accelerating DevOps velocity.
Leading practices for integrating IAM and PAM solutions
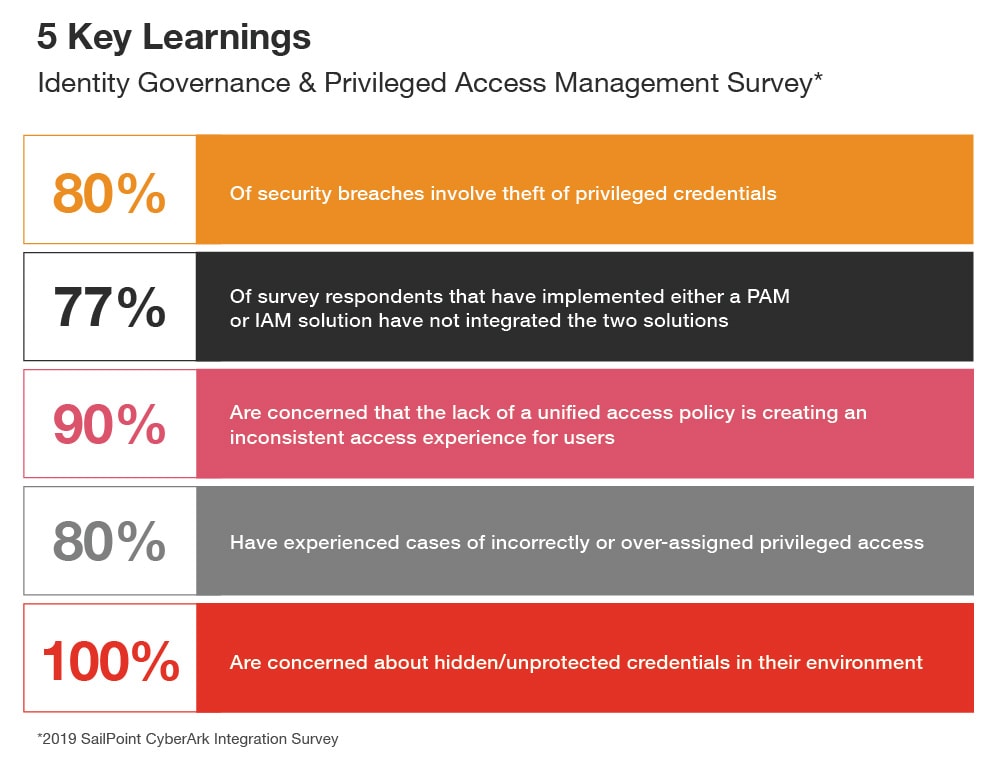
A recently conducted survey by PwC, SailPoint and CyberArk revealed that over 77% of organisations have yet to integrate their IAM and PAM solutions—exposing them to insider threats and cyber breaches. This white paper describes best practices for integrating IAM and PAM solutions and highlights the risks and challenges faced by organisations that have not properly integrated both solutions, to provide a unified view of user access.
The value we bring to CyberArk

Implement with an experienced cybersecurity team
CyberArk’s powerful privileged access management solution is backed up by our vast PAM experience, with over 120 dedicated PAM professionals serving 100s of enterprise clients. We combine a business mindset and a proactive digital transformation focus. You’ll be able to see around the corners of your PAM project, anticipating change rather than reacting to it.

Build buy-in from the top down
Cybersecurity is no longer the exclusive domain of the security team. The entire company, including its senior leadership, must understand that cyber risk is a holistic business risk. We help you build strong, visible leadership from the very top, so you can appropriately address your risk challenges and keep critical enterprise-wide programs up to date.
Threat-based deployment that meets your unique risk needs
We work with you to identify high-risk and high-value assets, and then begin to build an appropriate security strategy around them. Your processes and workflows, weaknesses and threats, system architecture and future state plans will all be leveraged. The correct fit and fill is never straight out of the box.
Focused PwC and CyberArk solutions in action
PwC has an extensive business relationship with CyberArk and has deep experience architecting and implementing CyberArk solutions across multiple industry verticals such as Financial Services, Healthcare, Energy & Utilities, Consumer & Retail, Industrial Products and Technology.
- PAM Implementation Methodology
- Rapid Onboarding Model
- Secure High Velocity IT
- PAM in Cloud
- Analytics Dashboard
PAM Implementation Methodology
PwC has a robust methodology that leads business lines through large and complex PAM implementations in familiar “SDL-like” phases that can be tailored to fit the client's implementation methodology.
Rapid Onboarding Model
PwC's onboarding methodology can be used for accelerated application onboarding after the establishment of the CyberArk foundational solution in a sprint-based approach leveraging proprietary accelerators across parallel workstreams to reduce risk through management of top tier privileged accounts.
Secure High Velocity IT
PwC has strong capabilities in working with clients to identify, design and deploy improved processes and security solutions for DevOps, such as CyberArk Dynamic Access Provider (DAP). Our experience in working with CyberArk DAP (Conjur) lets IT organisations efficiently manage access and authorization of privileges across the DevOps pipeline and also helps security teams mitigate risks and improve compliance without impacting Business-as-Usual workflows. PwC and CyberArk can help organisations build a secure and agile DevOps pipeline to achieve secure high velocity IT.
PAM in Cloud
Security is paramount when deploying PAM on the cloud since it holds the “keys to the kingdom”. PwC's Hybrid/Cloud PAM deployment methodology helps clients securely implement CyberArk PAS and DAP solutions in single-cloud, multi-cloud, or hybrid IT environments, leveraging inherent advantages that come with cloud platforms around dynamic scaling and availability, without compromising security.
Analytics Dashboard
Developed by PwC, the Analytics Dashboard is a web application that integrates with CyberArk PAS solution providing extensive reporting capabilities with a centralised and user-friendly view of the compliance status of privileged accounts, PAS components and privileged activity for PCI, SOX and Internal Audits.












